LinkedIn comes of age! Today marks 18 years since the launch of the world’s largest professional network for business, enterprise and employment use. However, like any social network, we must be aware of cyber-attacks and risk situations that we may face when using it. For this reason, we leave you with 5 key recommendations to use Linkedin safely:
- Use a unique, strong and different password.
Change the password periodically (every 3 months), do not use the same password for different applications and robust: more than 10 characters, with capital letters, numbers, punctuation marks and symbols. And remember, the password is only the user’s. Don’t tell anyone your password, and never write it down!
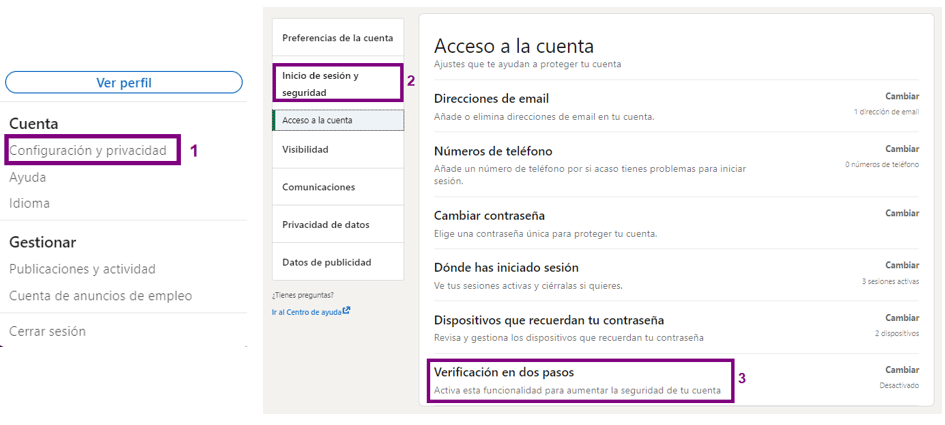
- Enable two-step verification.
It is one of the most frequent recommendations when we want to improve the security of our accounts, as it reduces the chances of identity theft and unauthorized access to confidential information. It requires a person to use more than one form of verification to access an account, usually “knowing something”, such as a password, and “having something”, such as a cell phone.
To set up two-step verification, follow these steps:
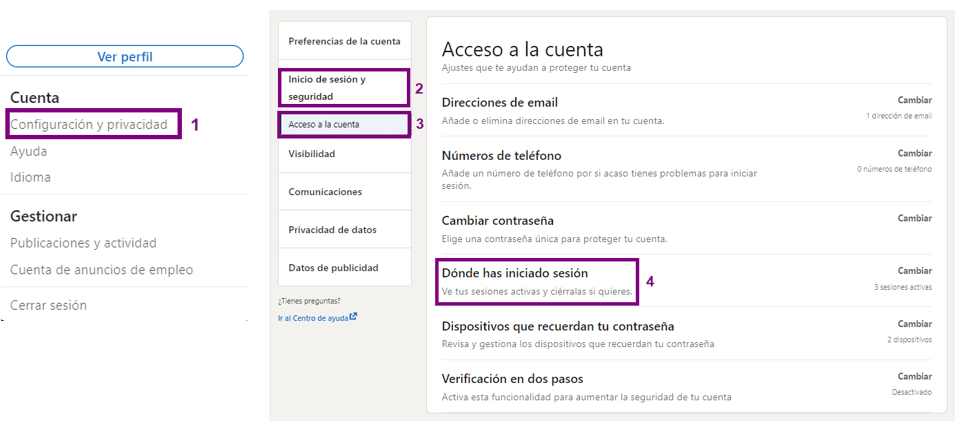
- Periodically review your active sessions the sessions you have active.
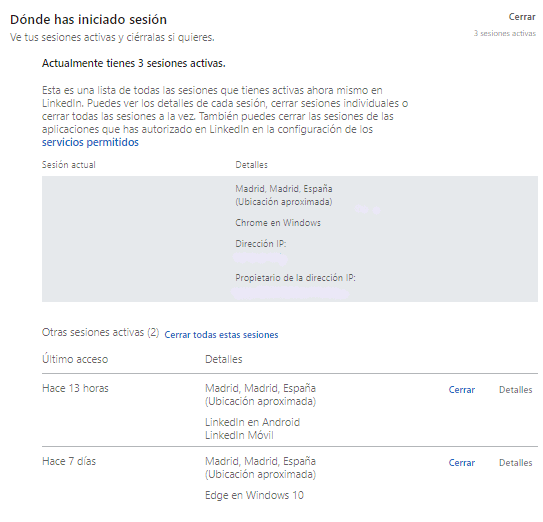
Details of each session can be viewed, showing the approximate location, the browser logged in, the IP address and the owner of the IP address. From here you can also close individual sessions or close all sessions at once.
A list of all currently active sessions will be displayed:
- Report spam, offensive and inappropriate content, phishing or suspicious messages.
In order for LinkedIn to review the alleged infringing content, we have to warn of these cases, and if necessary, always taking into account the definition contained in the Community Standards and Terms of Use, LinkedIn will remove them.
- Review the management of your personal data.
LinkedIn collects a lot of data about users through their profile.However, since recently, we can manage them. To do so, follow the steps below:
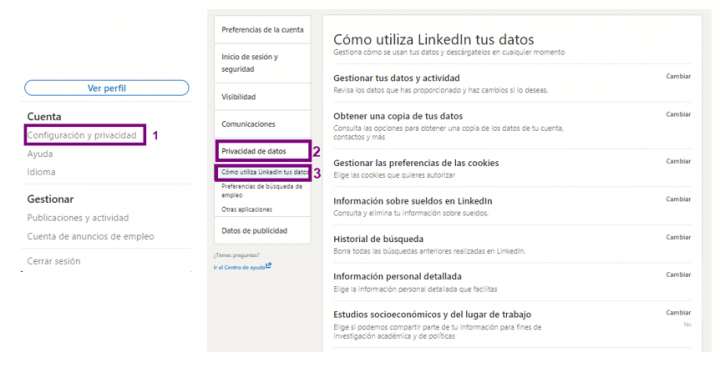
From this section you can view, manage and modify how LinkedIn uses your data and activity, you can download data at any time, you can get a copy of account data, contacts and more information, manage cookie preferences, choose the detailed personal information you provide and choose whether you want them to share your account information for academic research and policy purposes.
Through this route, you can access the personal data management:
By following these brief recommendations we can reduce the risk of suffering different types of cyber-attacks and of overexposing our data.
