We live in times of continuous change and technological transformation. On many occasions, these advances are not accompanied by the necessary security measures, like ethical hacking, facilitating the appearance of security breaches that can be maliciously exploited.

Hacker vs. cybercriminal
At this point is when the figure of the hacker appears, but what is an Ethical Hacking? It is very common to fall into the widespread idea that a hacker is a criminal, an obscure figure who is dedicated to stealing or collapsing computer systems, either for fun or for financial gain, but this is just the image that Hollywood has created for us.
A hacker possesses very advanced computer and technological knowledge, which allows him to “play” with technology as he wishes, and in many cases, to breach the systems he intends. However, this does not mean that they are criminals, but rather that they are often the greatest security allies a company can have. A large number of organizations and states have hackers in their ranks as security auditors, so that they can assess their systems and breach them before a real criminal does so.
But, if a hacker is not a criminal, how can a criminal with no technological knowledge breach a system? As in all aspects of life, there are professionals in the service of good or evil. This means that while a hacker is not a criminal, there are many people with the same knowledge who use them to perform criminal activities, such as deploying ransomware (data hijacking), spyware (spyware), cyberwarfare, system intrusion, etc. These users are known as cybercriminals and are very different from hackers.
Unlike a cybercriminal, a hacker seeks to discover vulnerabilities in systems, then report them and implement a quick fix. This is why cybercriminals should not be confused with hackers, since, although they are the same user profile, their activities and goals are completely different.
The thin red line

There is a fine line between right and wrong in aspects of hacking. On many occasions, hackers, for mere hobby or amusement, seek to break other people’s systems without authorization. Even if they subsequently report this situation to the company to address their security breaches, these actions can earn the entire collective a bad reputation, as has been the case throughout history.
On a daily basis, hackers perform penetration and intrusion tests on various organizations by simulating the steps of a cybercriminal. The knowledge is common, the only thing that comes into play is the individual morality of the person and that he/she is not corrupted by finding a possible economic source in one of these intrusion tests. For this reason we speak of Ethical Hacking.
Cyberwar
Let’s move on to a hot topic that has been affecting us all in recent weeks: war and its new areas of action, specifically cyberwarfare.
As we mentioned at the beginning of this article, we live in a society that is increasingly influenced by technology. Essential services are controlled by computer systems that are often vulnerable to attack. In a war context, the disruption of enemy communications and supplies, carried out in a cybernetic manner, has the advantage of zero exposure, as well as critical effectiveness and impact on the enemy in the event of a successful operation.
Today, all first world countries have a team of hackers in their ranks: their “cyber army”, both defensive and offensive. They are used to cope with the different waves of attacks that your facilities may suffer. And also to carry out attacks on their enemies, weakening their infrastructures and being able, occasionally, to end a war in a single cyberattack, if the security of a nuclear power plant were to be compromised and exploded… So the importance of these figures is enormous at present.not only at the military level, but also at the business level.
The value of our work
I sometimes hear that cybersecurity is expensive. However, during the years of experience auditing companies we have discovered hundreds, even thousands, of critical vulnerabilities and entered into the systems(exploitation). We have detected breaches of sensitive information, which, if they had fallen into the wrong hands, could have caused companies millions of dollars in losses, or even bankruptcy.
So, with this information on the table, is it really a bad investment to invest in cybersecurity? Is it a bad investment to have an ethical hacker in your ranks?
From what we have been saying, it is unlikely that today an armed and masked individual will enter your company to rob you, he will try to do it from his home, through the Internet. Faced with this situation, ethical hacking is the security points. For this reason, it is essential to incorporate these profiles in companieswhether auditing or advising on cybersecurity, since the panorama in Spain and Europe is that we are far behind in terms of IT security.and many readers would be shocked if they really knew the level of security that exists and what it entails.
Once again, prevention is better than cure, and just as we invest in physical and perimeter security, it is essential to invest in cybersecurity as times change, criminals adapt faster than organizations and organizations are exposed to their will.
A growing threat
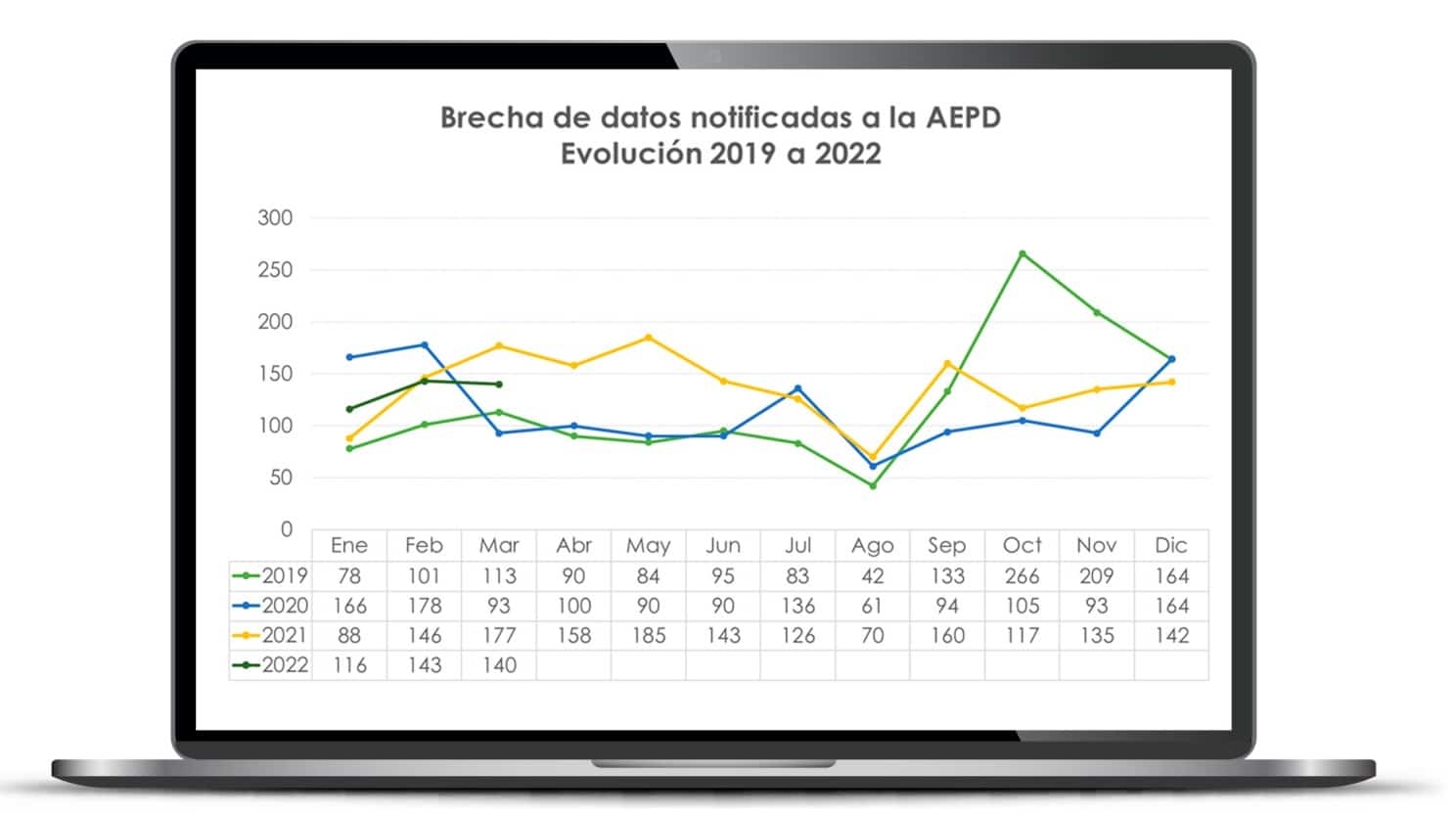
To further emphasize the importance of paying attention to the real and constant threat of cyber-attacks, we can look at the data recorded by the AEPD. As shown in the graph of the evolution of reported data breaches -security incidents that expose sensitive user data – to the Spanish Data Protection Agency (AEPD), in 2020 and 2021 there was an increase in the 20 percent more notifications than in 2019, and data for the first months of 2022 confirm the trend.
In its latest report, the AEPD notes that “a considerable number of personal data breaches have phishing as a vector of entry into organizations.
phishing
as a vector of entry into organizations. Cybercriminals use emails that include links to pages that impersonate access portals to popular cloud productivity tools to obtain login credentials and other data that they then use.”
The organization recommends
training and awareness campaigns
to employees to avoid this situation. “Special attention should be paid to emails and messages with links, documents and executables attached,” the report states.
In closing, I would like to recall the popular saying “nothing ever happens until it happens“. If governments have a multitude of hackers in their offices and leading companies already have these profiles, won’t they be more important than we usually give them? Just look up how many companies went bankrupt in 2021 due to cyber attacks and then start raising awareness of the importance of cybersecurity and ethical hacking.
Carlos Gómez Pintado, Offensive hacking line leader in Grupo Oesía
