In 2016, OIOS was notified of the existence of applications in the Department of Health that were installed without any type of restriction, which made the organization more vulnerable to failures and attacks, as well as to non-compliance with regulations. All this taking into account that we are in such a sensitive sector and with such a high value on the black market.
In this sense, and pursuing to make effective the provisions of the General Data Protection Regulation 2016/679, of April 27, 2016, on the principle of proactive responsibility, which translates, among other things, into implementing adequate controls to mitigate risk, as well as measures to ensure privacy from the design, understanding this as the application of data protection guarantees from the initial planning phase for any technological development. On the other hand, it also implies privacy by default, understood as the application of measures to ensure that only the data necessary for the intended purpose are processed.
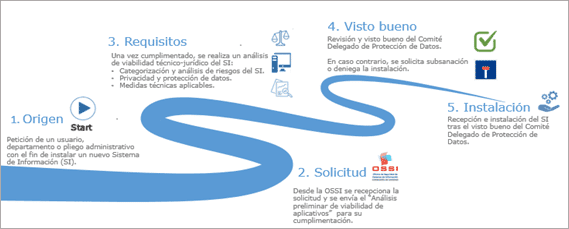
To this end, for each new information system project, an initial document must be created to define the scope and scope of data processing and security measures, providing basic information to ensure the viability of the application.
Additionally, in the First Additional Provision of Organic Law 3/2018, of December 5, on Personal Data Protection and Guarantee of Digital Rights, it is indicated that Public Administrations have the obligation to implement and comply with the provisions of the applicable National Security Scheme.
OIOS is developing an analysis methodology based on the performance of an "Preliminary analysis of application feasibility". (AVA), which aims at the preliminary analysis of the application, in order to detect basic problems that may be encountered in the future, and the preliminary feasibility (or not) of the same, giving the responsible the opportunity to solve the initial problems that have been detected.
The AVA includes a series of specific questions aimed at gaining in-depth knowledge of the functionality of the application, as well as the specific security measures provided for in the provisions of the ENS and RGPD.
In this document, in addition to the technical specifications for the implementation of an application, an additional review is made from a data protection perspective, in order to verify that the organization that has requested the installation of any application has previously informed.
Based on the information provided, OIOS issues a series of recommendations aimed at ensuring that the application has the necessary measures to guarantee compliance with data protection and information security. Subsequently, the recommendations issued are validated and signed by the CSCM's Data Protection Delegate Committee, in accordance with the competencies set forth in the GDPR on the supervision of the provisions contemplated therein.
This methodology is intended to be an effective and preventive privacy control from the design stage, taking into account that no application will be installed in the CSCM without the approval of the OSSI and the CSCM's Data Protection Delegate Committee.
OIOS issues a series of legal-technical recommendations on the information systems under analysis, so that the responsible organizations can incorporate the proposed improvements or compensatory measures prior to putting them into production.
If deemed necessary, meetings are held with the necessary participants to clarify those aspects considered relevant.
During the course of the analysis it is common to request corrections due to lack of information, or even to determine that the system is not viable.
Currently, and understanding the technological advancement driven by the exceptional situation of COVID-19, the analysis of applications that contemplate advanced technologies based on Big data, Iot, AI has substantially increased. This has involved, among other things, the supervision of anonymization processes to ensure the irreversibility of the data.
Likewise, with the fall of the privacy shield, the number of applications that did not have the necessary guarantees for making international transfers has increased, making it necessary to carry out a detailed analysis of these applications.
The legal and technical control before putting the applications into production has made it possible:
SGoSat is a family of high-tech SOTM (Satellite Comms On The Move) terminals that are installed in a vehicle, providing the ability to target and maintain a stable connection to the satellite when the vehicle is in motion in any type of conditions.
The SGoSat family is composed of versatile terminals, which can be installed on any type of platform: trains and buses, military and/or government vehicles, aircraft, ships, etc. Originally designed for the military sector, SGoSat terminals are extremely reliable and robust, integrating high-performance components that comply with the most stringent environmental and EMI/EMC regulations. The product uses low-profile, high-efficiency antennas and a high-performance positioning and tracking unit, allowing the terminal to be operated anywhere in the world.
In order to meet the diverse needs of its customers, INSTER has developed single band and dual band terminals in X, Ka and Ku frequencies.
The SGoSat family of terminals can also be configured with a wide range of radomes (including ballistic options) to suit customer requirements.