cybersecurity and encryption
RAGNAROK
Ethical Hacking
TO UNLEASH THE STORM, TO LEARN TO LIVE IN THE RAIN
The solution that tests the security of your systems and the real strength of your business against a cyber attack.
Ragnarok is the strategic solution to know the real situation of your cybersecurity systems and strengthen them against different disruptive situations.
Knowing your vulnerabilities in time to strengthen your systems
Learn how a cybercriminal might proceed to carry out an attack
Thanks to the different service modalities and our cyber experts, we are able to find key vulnerabilities, allowing the mitigation of security risks.
All our services are performed with the utmost confidentiality, as well as in accordance with the best international cybersecurity standards and practices.
Cybersecurity in figures
The 360º scope
of Ragnarok
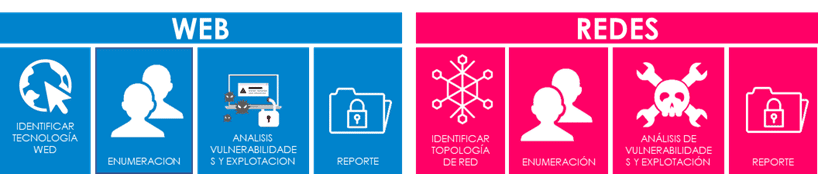
The Ragnarok model is comprised of two elements differentiated by the nature of the assets targeted for testing, both teams focus on detecting what the tools cannot do on their own. On the one hand, the Web team is in charge of WEB applications and services, while the Network team is in charge of detecting and exploiting vulnerabilities in corporate networks.
With Ragnarok we can evaluate these environments.
Who trusts us







































































What do we do?
Ragnarok works with innovative processes, focused on discovering advanced attack paths tailored to the client's profile. It is based on the constant updating of hacking techniques and vulnerabilities publicly registered by official bodies such as MITTRE or NIST.
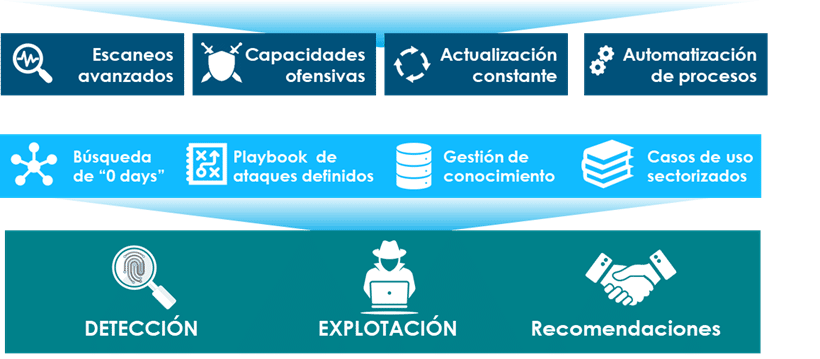
Comprehensive reviews and simulations of real risk situations
We go where machines can't, but humans can.
WEB AUDIT
Identify vulnerabilities and weaknesses of web platforms and applications in the network within the scope to be audited, as well as the services they offer. Using the OWASP Top 10 standard.
MOBILE AUDIT
The vulnerabilities and threats of the applications are identified both at the application level and at the code level, using the OWASP MOBILE SECURITY standard.
CODE AUDITING
It consists of performing an in-depth analysis of the application to detect vulnerabilities that allow the improper use of an application using our Oesía CODSEC methodology.
WIFI AUDIT
We contribute with the recognition and collection of vulnerabilities found in wifi networks based on the OWISAM security standard.
PENTESTING
Identify vulnerabilities and weaknesses of the systems and services deployed in the networks within the scope to be audited. OSSTM 3.0 methodology is followed.
SOCIAL ENGINEERING
It consists of measuring the level of cybersecurity awareness of an organization through the methods most known to a cybercriminal.
FORENSIC ANALYSIS
Activities to detect the consequences of a previously suffered attack based on the preservation of evidence methodology.
IOT AUDIT
Analysis of hardware vulnerabilities in embedded devices to prioritize mitigation tasks and reduce risks in an agile and effective way.
Our
packs
From the Technical Security team of Oesia we provide our clients with the technology, the processes and the expert team necessary to test the client’s assets and find weaknesses to prevent future damages in case of cyber-attacks.
All of our
solutions
in cybersecurity
Our solutions enable us to provide our customers with the cybersecurity services they need.
Increases the level of
security
of your company
Contact our cybersecurity specialists and they will advise you on what is best for your company.
Phone
+34 91 309 86 00