Brief History of Cyberspace
At its origins in the late 1960s, the Internet was created as a secure communication tool. With the development of the first e-mail in 1972, what we know as the “e-mail” came into being. open networkswhich allow free communication between people. The amount of information shared increased so much that it was necessary to create two elements:
1 – Search engines

keywords
that represent the content we are looking for, and redirect us to different websites related to it.
In this sense, Google brought about a revolution by presenting search results according to their ranking or hierarchy, based on the number of times users entered the indexed web pages.
2 – Architecture by levels or layers
It is the segmentation of cyberspace into
cyberspace in layers
or “protocols”, depending on how easy it is for users to access the information. In summary, there are two types of protocols: those that involve indexing content to search engines, and those that avoid indexing content.
Thus, there are two layers in cyberspace: the Surface Web and the Deep Web.
Surface Web: the Internet of Things
It is the most superficial layer of cyberspace, and is aimed at the use of known and public Internet resources and content, which can be accessed from any browser.
can be accessed from any browser
. These resources and content have been filtered, categorized as “clean” and “public” and then indexed to search engines.
But the Surface Web is not exempt from vulnerabilities, cyber-attacks take place on it on a daily basis: the Phishing message we receive in our email, when our identity is impersonated in our social networks, or when we browse fake pages that have managed to overcome the limitations imposed by the requirements and protocols of this layer.
What are the mysteries of the Deep Web?
The Deep Web, also called the Deep Web, encompasses all websites not indexed by traditional search engines, and is estimated to represent between 90-95% of all information on the Internet.
90-95% of all information found in cyberspace.
found in cyberspace.
It is not a physical network separate from the Internet of Things, but a layer of application and cyberspace protocols that restricts access to sensitive, secret or encrypted information. For example, all private DropBox content is part of the Deep Web, as it cannot be indexed.
How do I navigate the Deep Web?
This layer of the cyberspace network can only be accessed with specific software. The most popular is the Tor network, but i2p, Freenet and ZeroNet can also be used.
The Tor network, by its acronym,
The Onion Router
protects the anonymity of users for their access to the Web through encryption. The searches work with predefined routes of globally distributed private nodes, interconnected with each other and contributed by anonymous volunteers, which manage the communication flow between sender and receiver.
What are the dangers of the Deep Web?
The truth is that there are many
myths and creepypastas
about what happens in the Deep Web, since it is often confused with the Dark Web, which we will talk about later.
We must always remember that any tool can be used for illicit and criminal purposes. And it is not as if we are going to receive a cyberattack as soon as we enter the Tor network; in fact, most of the information on the Deep Web is, to a certain extent, harmless.
When surfing the Deep Web, we simply need to take extreme
simply take the measures we already
that we already apply in the Internet of Things to avoid becoming victims of cybercrime such as fraud, information theft or the execution of malware files.
Dark Web, the greatest danger of the Deep Web
Of all the resources we find on the Deep Web, studies confirm that
approximately 0.1% is part of the Dark Web.
. Its routing is more robust and complex than the usual Deep Web routing, and allows surfers, thanks to the anonymization of the Tor network, to perform and share any activity in a protected way.
The Dark Web is so called because of its totally private content, and its anonymity is exploited in three typical scenarios:
- On the part of political dissidents and whistleblowers to share information, to express their opinions by circumventing imposed censorship, or as a desperate means of secure communication.
- By cybercriminals for the commission of a variety of criminal acts, some of them extremely pernicious.
- By researchers and researchers and journalists to communicate with subjects of interest and/or find information through OSINT methods.
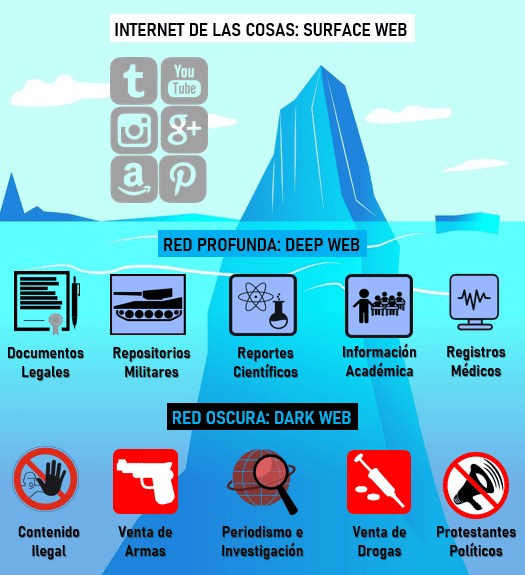
Among the most prominent criminal activities on the Dark Web, we find the following DarkNets or dark sub-networks:
- Crimes against public health:
Such as the purchase and sale of all types of drugs and medicines. - Training forums:
these indoctrinate new users to support extremist, terrorist and/or criminal ideologies. - Pages with illegal services:
sale of stolen credit cards through Carding or Skimming, of all kinds of weapons, fake documents, black hat hacking services, money laundering, and even services of hired assassins and mercenaries. - Content pages:
the content on these pages is often pernicious and violent.
All sales and purchases made on the Deep Web, and by extension on the Dark Web, are made using
cryptocurrencies
The encryption of cryptocurrencies allows the identity of both parties to be safeguarded.
In addition, many services are actually
scams
created by cybercriminals seeking to infect our devices, usually with ransomware. They may also be law enforcement officers working in an undercover operation.
Regarding the illegal contents of the Dark Web, it should be noted that participating in them is a criminal offense, since accessing them usually requires sharing illegal contents in the first place. Remember that creating, sharing and/or viewing illegal content is a crime.
As Internet users, we have not missed anything on the Deep Web, let alone the Dark Web. Remember that Darknets are cyberspaces that are totally outside the law, and only experts from the competent authorities should access them.

